This article describes the required roles you have to assign to your technical user(s).
SAP Process Orchestration (Technical User) Roles
- SAP_XI_API_DISPLAY_J2EE
- SAP_XI_APPL_SERV_USER
- SAP_XI_MONITOR_J2EE
- SAP_PI_B2B_TPM_ADMIN
- SAP_BPM_ODATA
- SAP_BPM_SuperAdmin
- To be able to Stop communication channels, you also need to create a new role (e.g. WHINT_MMA with the following Actions (type J2EE):
- com.sap.aii.af.app: xi_af_channel_admin_modify
- com.sap.aii.monitoring.remoteapi: xi_af_channel_admin_modify
SAP ABAP System (Backend , e.g. S/4HANA, ECC)
- Role (or authorization objects of this role): SAP_XI_APPL_SERV_USER
- Authorization Object S_RFC – RFC_TYPE: FUGR, Activity: 16, RFC_NAME:
- RFC1
- SDIFRUNTIME
- SDTX
- SYST
- SYSU
- Authorization Object S_TABU_NAM – Activity: 03, TABLE:
- CRMRFCPAR
- EDIPOA
- EDIPOD
- EDIPOXH
- EDP13
- EDP21
- PATH
- PATHTEXT
- QSENDDEST
- RFCATTRIB
- RFCDES
- SRT_CFG_DIR
- SRT_RTC_BNDG
- SRT_RTC_DATA
- SXMSCONFVL
- SXMSINTERFACE
SAP Cloud Integration Roles (Neo)
- IntegrationOperationServer.read
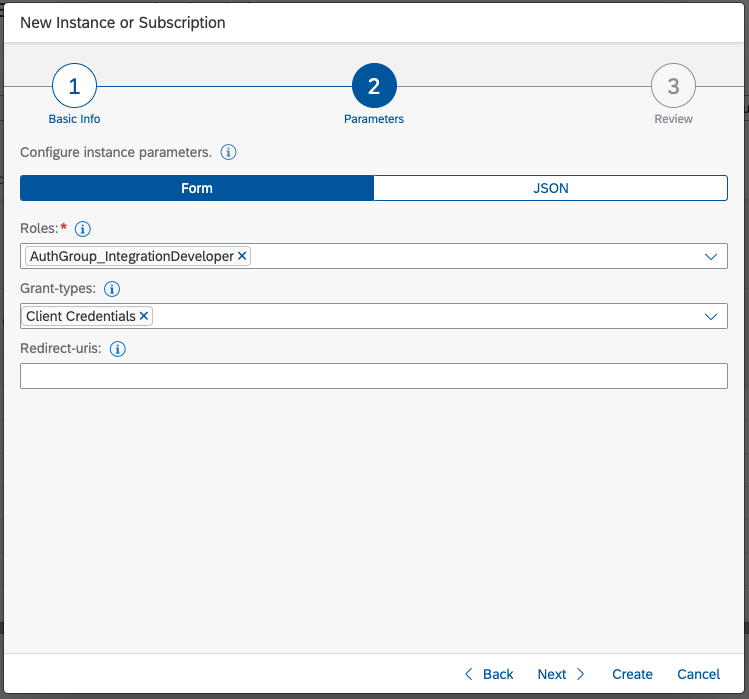
- AuthGroup.IntegrationDeveloper
- AuthGroup.Administrator
SAP Cloud Integration Roles (Cloud Foundry)
- PI_Integration_Developer
- PI_Administrator
SAP Cloud Integration Service Key for OAuth (Cloud Foundry)
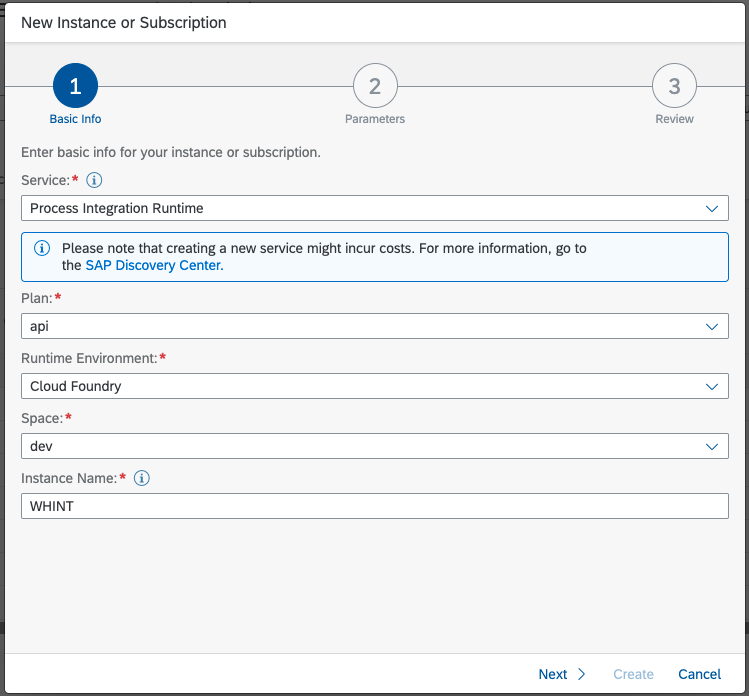
Create a Service Instance (e.g. “WHINT”) of type “Process Integration Runtime” with plan “api”.
SAP API Management Service Key for OAuth (Cloud Foundry)
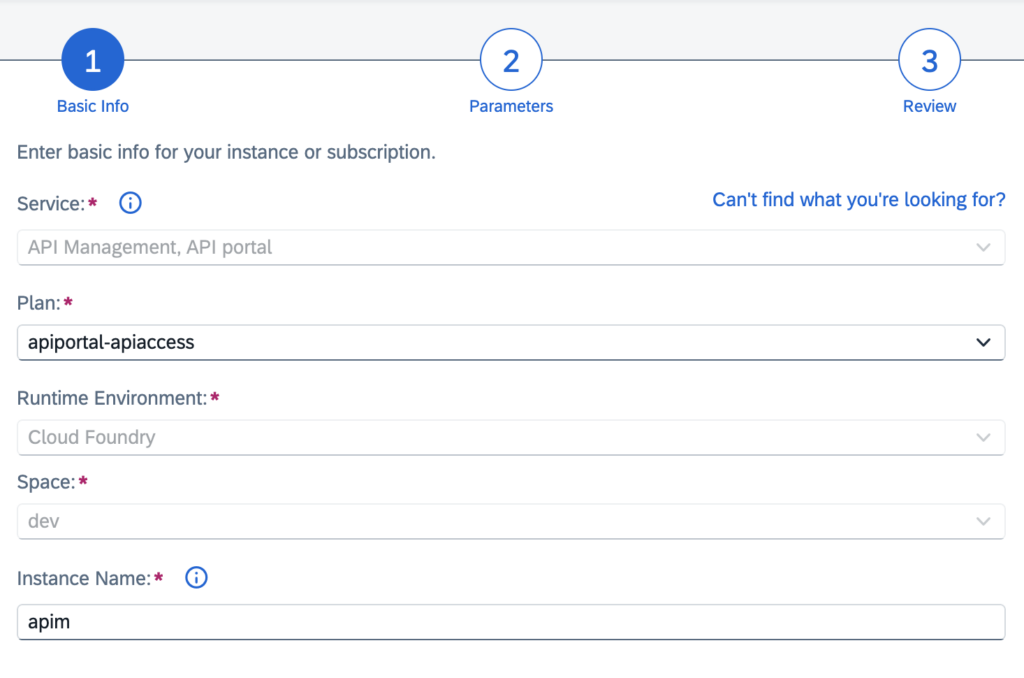
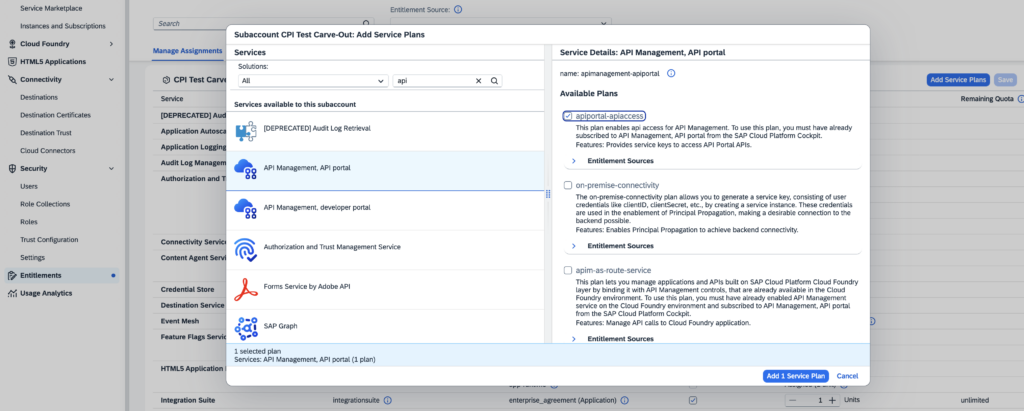
Create a Service Instance (e.g. “apim”) of type “API Management, API portal” with plan “apiportal-apiaccess”.
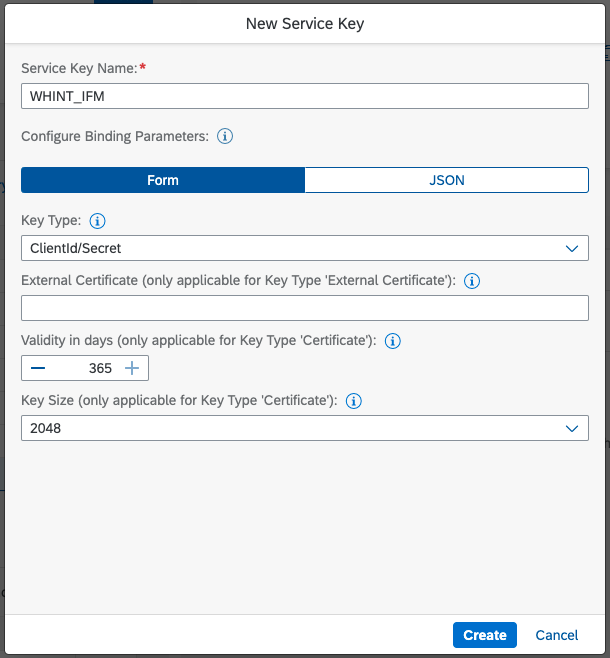
Create a Service Key (like for Cloud Integration) and use the credentials in the configuration.
All required information is provided in the details of the Service key:
- URL (to access the API)
- Token URL, Client & Secret (for the OAuth access)
If you don’t find the service in your Service Catalog, you need to add the entitlement first:
Microsoft Azure (Integration Services)
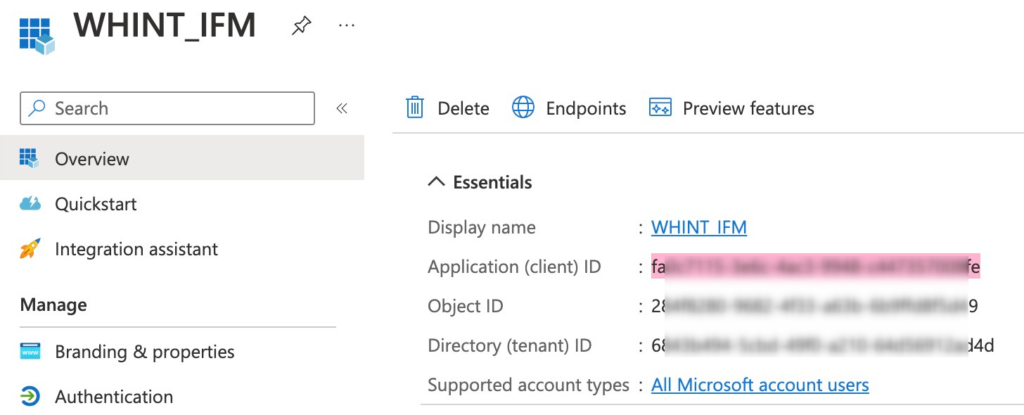
- Create a new app registration, e.g. “WHINT_IFM”
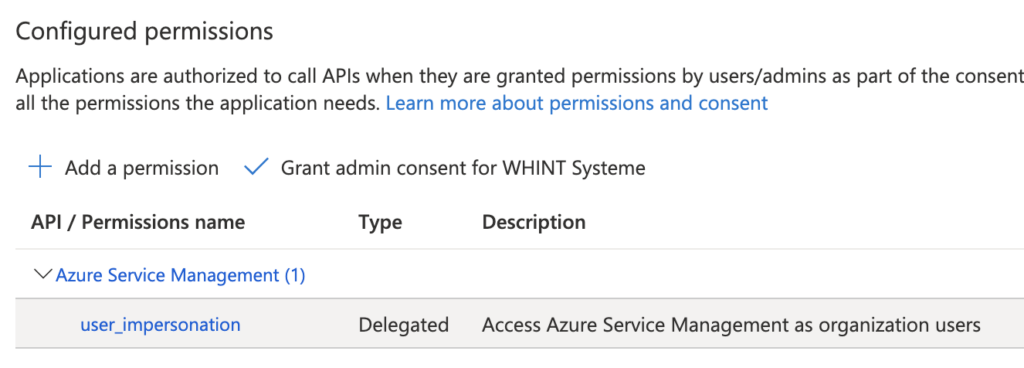
2. Add API permissions for Azure Service Management
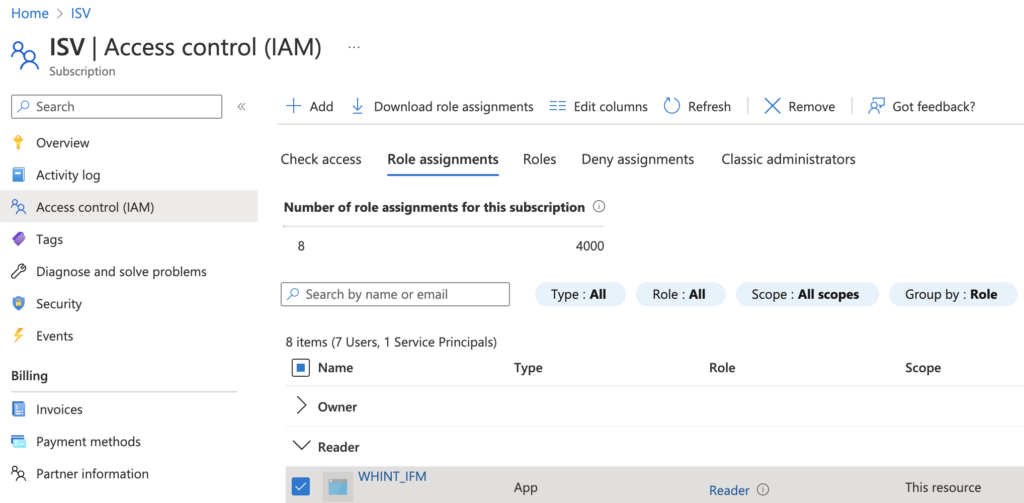
3. Add role-assignment ‘Reader’ for the app reg. to the subscription
4. Create a client secret and store the value (will disappear afterwards) – ignore the client id here
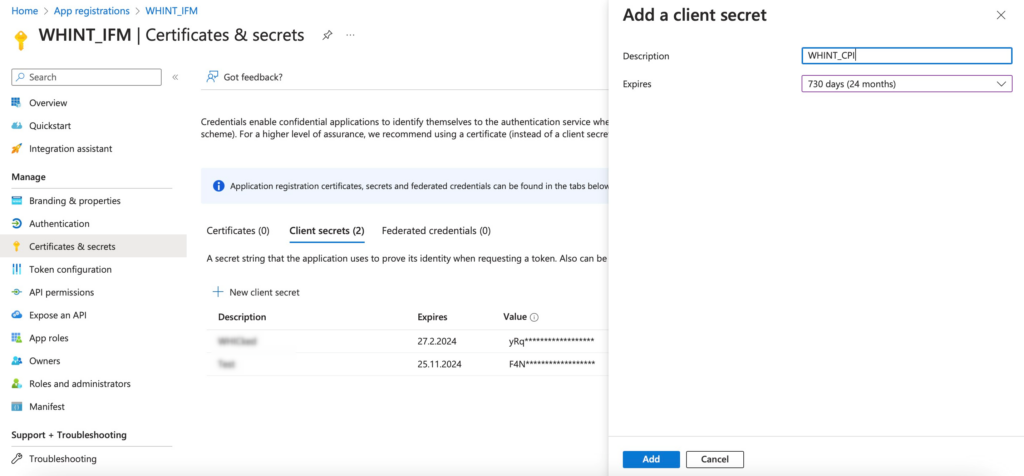
For the API access, please provide:
- Token Service URL: <from step 1: Directory (tenant) ID>
https://login.microsoftonline.com/<tenantID>/oauth2/v2.0/token - Client ID: <from step 1: Application (client) ID>
- Client Secret: <from step 4>